Security researchers have uncovered a new breed of Android ransomware named DoubleLocker which has been spreading recently. This ransomware can not only encrypt all your device data but will also lock your phone and change the PIN required to unlock the target device. Since the device gets locked, it is almost impossible for users to recover their data without paying the ransom demanded by the hackers.
This new Ransomware is getting distributed through a fake Adobe Flash Player Apps which are circulated through certain compromised websites. Users who are not aware of this might install the ransomware which will ask for Administrative Permissions once installed and then makes itself as the default home application. The ransomware gets activates when the user hits the home button and the device gets locked again. But the user will be unaware of the fact that whenever the home button is pressed, the malware gets activated. Once active, the malware will change your PIN to random number which is not stored on your device.
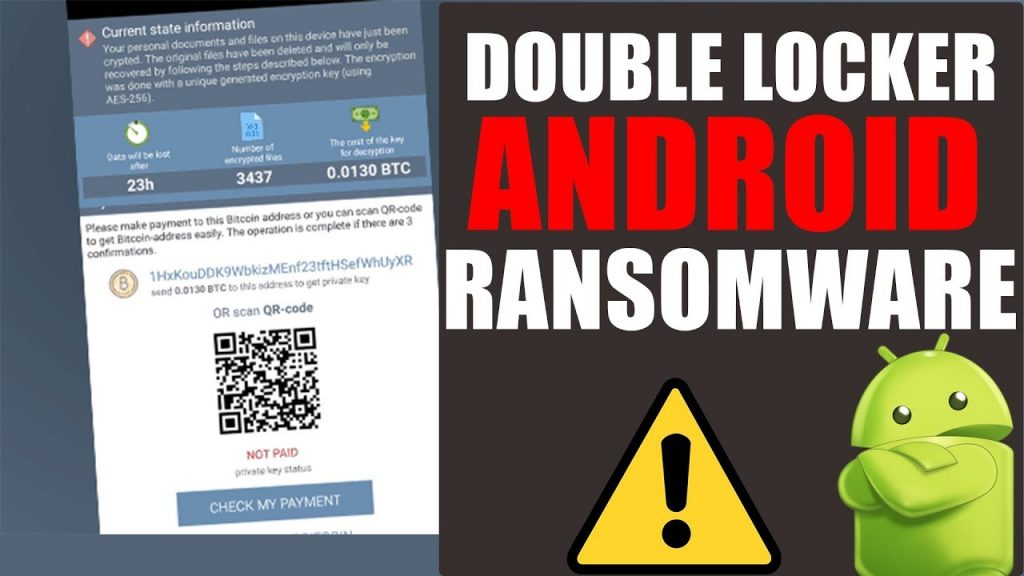
The DoubleLocker ransomware will encrypt all your data files in the primate storage directory of your Android phone or tablet using the AES (Advanced Encryption Standard) algorithm and the “.cryeye” extension. If you don’t have the encryption key, there is no way to decrypt and recover your files since AES is the most powerful encryption algorithm. The hackers are usually demanding a ransom of 0.0130 Bitcoins (BTC) which is equivalent to 54 USD or 4000 Indian rupees as of today. Also, you should pay the ransom within 24 hours in order to recover your data.
DoubleLocker was first discovered by the IT security professionals at ESET which sells Antivirus software and other Internet Security solutions. The researchers have stated that this ransomware abuses the accessibility settings in the Android device and is the first-of-a-kind malware which makes use of double-lock approach. There was a similar malware targeted at banking applications which is considered to be the test version of this DoubleLocker malware.
Lukáš Štefanko, a malware researcher at ESET who found the DoubleLocker says that the malware disguises itself as the default home app in the Android phone and launcher which makes it persistent. This is an intelligent trick used by the designers of the malware to get it activated whenever the user clicks the home button. The Accessibility service in Android devices allows for this loophole which hackers can use to launch malware without getting the user alarmed.
After Petya and Wanna cry Ransom-ware which were targeted mainly towards PCs and Desktops, the malware developers have turned their attention towards Android devices. Since the DoubleLocker gets the administrator permission, it gives complete remote control of your device to the attacker who can change passwords, locate, remote lock or wipe all your data.
Users have to do factory reset in order to gain access to the phone but all the data will be lost. Users having rooted phones can gain access without having to factory reset. They can connect their device to ADB in debugging mode and remove the system file which stores the PIN. By this method they can unlock the device and deactivate the administrative rights for the malware and later uninstall it.
Users should be careful when download and installing Apps from unknown sources on their phones. Also, you should avoid clicking on pop-ups which asks to install any new software or plugins on your device. You should never provide Administrative rights to unrecognized software which is really dangerous and gives complete remote access for the app developers to your phone.

